15 DDoS Attack Types and How to Mitigate Them
- Updated: Aug 27, 2024
- 7 min
All electronic systems have a limited data processing capacity. Typically, this threshold is never exceeded under normal conditions.
However, that can change when anomalous activity kicks in. A distributed denial-of-service (DDoS) attack is a strategy that can drain a web server’s resources and disrupt the associated online service.
Usually, Node.js developers manage protecting servers. However, not all startups have full in-house development teams. So, spreading awareness about DDoS attacks is necessary to help safeguard businesses.
DDoS attacks emerged in the mid-1990s as an ideological weapon groups like Anonymous and similar hacktivists used. Over time, the motivations have expanded – from script kiddies looking to satisfy their egos and get an adrenaline rush to unscrupulous businesses trying to undermine their competition.
The latest trend is extortion through so-called “ransom DDoS” attacks. Here, an adversary threatens to knock an organization’s website offline unless they pay a crypto ransom.
This article summarizes known DDoS attack methods and discusses effective countermeasures.
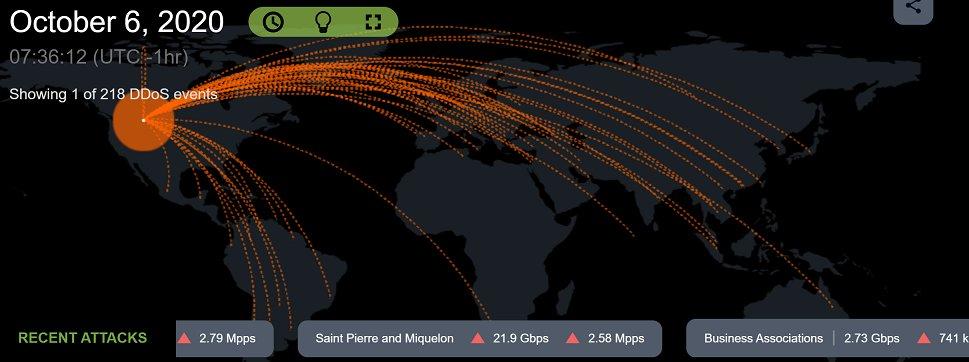
(Screenshot image by David Balaban, source NETSCOUT Cyber Threat Horizon )
Guard against downtime and data breaches with our expert DDoS protection tailored to your business needs — contact us today to get started!
Why DDoS Attacks Are So Dangerous
With organizations heavily relying on uninterrupted availability of their websites these days, service downtime entails reputational issues and customer churn, which translates to adverse financial implications down the line. Unsurprisingly, the above-mentioned extortion tactic with DDoS at its core is flourishing.
Tracking customer retention is essential, and this churn rate calculator can help measure your customer loyalty.
Since mid-August 2020, several high-profile hacker gangs, including the infamous Lazarus Group and Fancy Bear, have been sending such blackmail notes to thousands of companies around the world, primarily ones from the finance and retail sectors.
The felons demand a minimum of 10 BTC (currently worth about $106,000) for not mounting the attack. On August 28, the FBI alerted U.S. companies to the menace by issuing an ad hoc flash warning.
One more facet of the problem is that DDoS can be used as a red herring in data exfiltration or ransomware attacks. It creates “noise” that distracts a target company’s InfoSec staff from a more impactful threat, thereby impeding swift incident response.
An extra concern is that DDoS operators are increasingly adept at amplifying their attacks via huge botnets consisting of unsecured IoT devices. This approach was behind the most powerful assaults reported to date, including the 2016 Dyn cyber-attack that generated rogue traffic exceeding 1Tbps.
Common DDoS Targets in 2025
With the COVID-19 crisis being underway, the implementation of remote learning programs saw a dramatic spike this year, and so did DDoS attacks targeting the education and academic sector. Mostly orchestrated by hacktivists and rebellious students, these incursions lead to network downtime and disrupt virtual classes. There was also an increase in unwanted intrusions and malware infections in Mac and other devices used in day-to-day work.
Unethical business competition is another area where DDoS plays a role. For instance, malicious actors often swamp Minecraft servers to lure gamers into switching to another hosting service.
Cryptocurrency exchanges are common targets as well. By disrupting these services via DDoS-for-hire platforms, unscrupulous rivals encourage coin traders to look for alternatives.
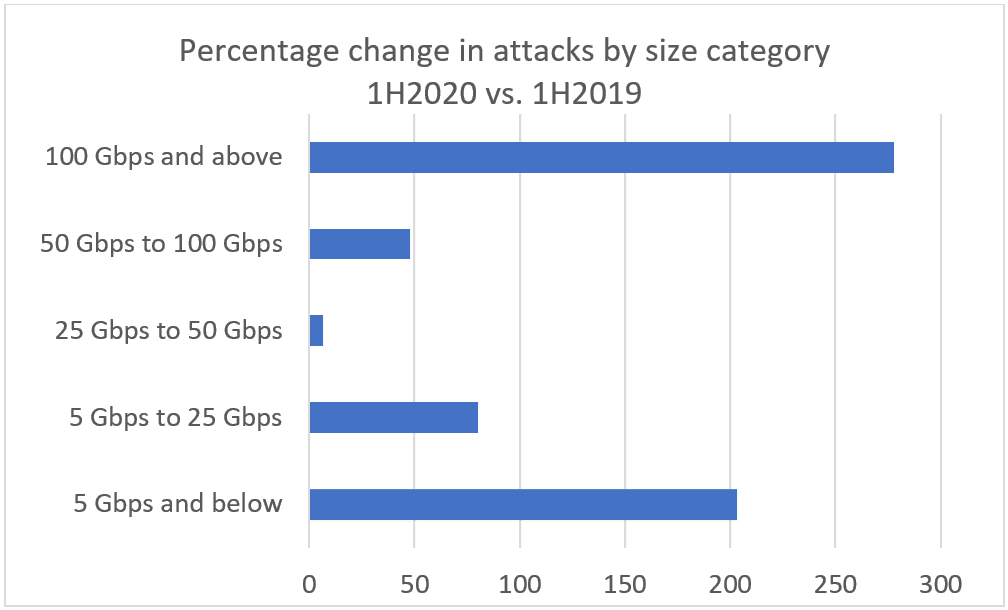
(Image source: Neustar)
During January through June 2023 compared to the same period in 2012, the number of DDoS attacks sized 100 Gbps and above grew an enormous 275%. At the same time, the number of small attacks, sized 5 Gbps and below, grew also by more than 200%.
15 Common DDoS Attacks
Security professionals single out numerous techniques that differ in the logic of precipitating a denial-of-service condition. To better understand the network disruption repertoire of the present-day crooks, go over a hands-on summary of the most common DDoS types.
- DNS Flood. To execute this incursion, malefactors deluge a DNS server with a huge number of malformed requests coming from numerous different IP addresses. This is one of the toughest attacks to detect and recover from. You can use DNS Protection as an added layer of security for prevention but this attack is one of the most dangerous large layer 3 attacks and so is very difficult to mitigate using the on-premises solutions.
- UDP Flood. An adversary fires out a slew of rogue User Datagram Protocol (UDP) packets at a victim server to make it run out of processing capacity. A serious pitfall in terms of identifying this attack is that UDP connections provide scarce methods to verify source IP addresses.
- SYN Flood. This foul play abuses the TCP three-way handshake, a fundamental mechanism used to set up a connection between a client, a host, and a server in the TCP protocol framework. Criminals flood a target server with multiple SYN (synchronize) packets coming from a rogue IP. For the record, the role of SYN packets in a benign scenario is to request a connection with a server.
- Fragmented ACK Flood. An attacker shells a network with patchy ACK (acknowledge) packets. When attempting to organize these requests, routers encounter a denial-of-service condition. This raid is one of the crooks’ favorites because it can disrupt a network with a comparatively small number of partial packets.
- Ping Flood. This DDoS attack revolves around fraudulent Internet Control Message Protocol (ICMP) echo requests. The victim server allocates all of its resources to spawn packets in response to these numerous pings and denies service to legitimate clients.
- HTTP Flood. To initiate this incursion, a threat actor shells a web application with malformed GET or POST requests. To imitate natural traffic, this technique may engage a botnet of previously infected devices.
- Ping of Death Attack. A malefactor deluges a network with ping packets that “weigh” more than 64 bytes, which is the maximum permitted size. The receiving server tries to reassemble these offbeat packets to no avail and eventually crashes.
- IP Null Attack. To launch this incursion, an evildoer targets a server with IPv4 packets in which the header value is set to null. These irregular messages confuse the server to the extent that it can no longer operate properly.
- Fraggle Attack. This foul play involves rogue UDP packets carrying a knockoff IP address of the target’s router. As a result, the network device replies to itself non-stop until it becomes incapable of reacting to legitimate requests.
- LAND Attack. LAND – short for Local Area Network Denial – is a raid relying on dodgy SYN packets in which the source IP and the destination IP are an exact match. The victim server is thereby pulled into a loop of iterative responses to itself, which causes a denial-of-service predicament.
- Slowloris. An attacker initiates a bevy of simultaneous connections to a web server and keeps them active by periodically adding split packets and HTTP headers. These connections stay uncompleted for a long time and waste the server’s processing capacity. On a side note, a single computer can be enough to execute the Slowloris onslaught.
- Low Orbit Ion Cannon (LOIC). Ideally, LOIC is used as a tool that allows security experts to identify the pain points of a network by stress-testing it. However, sometimes criminals turn the original purpose upside down by mishandling it to deplete a server’s resources with fake HTTP, UDP, and TCP packets.
- High Orbit Ion Cannon (HOIC). This is a LOIC spin-off with a much higher stress-testing potential under its hood. DDoS actors often hinge on it to generate myriads of HTTP POST and GET requests and knock a target server offline in a snap. Incidentally, HOIC can concurrently home in on more than 250 domains.
- APDoS. The acronym stands for “Advanced Persistent Denial-of-Service”. This mechanism kicks in when attackers blend a series of different techniques to deteriorate the performance of a network or a server. Another hallmark of this attack is that it usually lasts for weeks and withstands traditional incident response methods.
- IoT Botnet Attack. This is one of the most destructive types of DDoS as it can generate immense data transfer rates that reach several terabits per second. These attacks parasitize a network of compromised Internet of Things (IoT) devices to generate fraudulent traffic and route it toward a computer network.
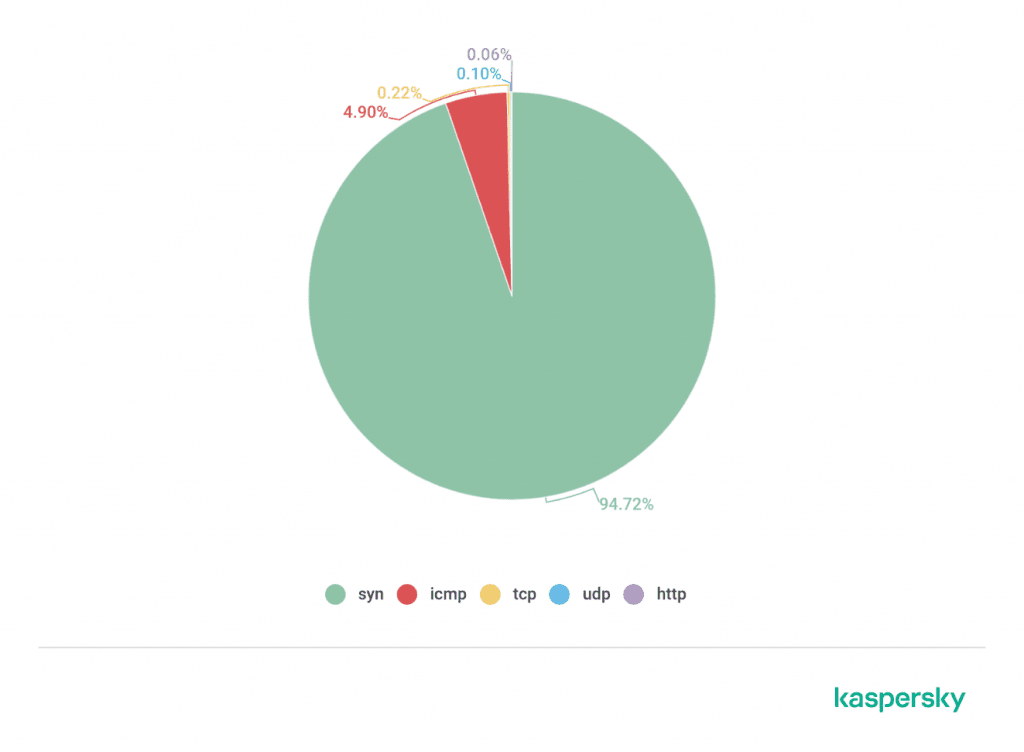
(Image source: Kaspersky Lab, DDoS Report Q2 2020)
According to Kaspersky Lab, SYN flooding is the most popular method for now. The share of SYN flooding is currently 94.7%. The leader is followed by ICMP flooding 4.9%.
Also, take a look at specific services, designed to deal with DDoS attacks. For example, Vulners create a powerful database not only for vulnerabilities but also for news. In their database, you can subscribe to all news with DDoS attacks.
From concept to creation – launch your marketplace with SPDLoad!
Best Practices for Mitigating DDoS Attacks
Here is a roundup of the most effective methods to fend off DDoS attacks:
- Use a cloud DDoS protection service. Outsourcing your defenses to a trusted cloud-based service such as Cloudflare, Sucuri, or Akamai is a reliable method to survive even the most powerful assaults or prevent ransomware attacks.
- Leverage a web application firewall (WAF). The role of a WAF is to monitor incoming Internet traffic and thwart web application abuse via cross-site scripting (XSS), cross-site request forgery (CSRF), or SQL injection.
- Step up your traffic filtering techniques. This tactic enhances a WAF through deep packet inspection, IP blacklisting, and rate limiting.
- Deploy an intrusion prevention system (IPS). An IPS will protect your network against malicious code and hacker attacks that try to exploit known software vulnerabilities.
- Perform code auditing. InfoSec teams should regularly sanitize the code running in an enterprise environment to ascertain that it doesn’t have any exploitable flaws. This is a countermeasure for application layer (layer 7) DDoS attacks.
- Keep your systems up to date. Timely updates are a hugely important element of DDoS protection. Vulnerability patches raise the bar for malefactors and prevent the network infrastructure from becoming easy prey.
- Use the most secure VPN. These kinds of services increase your overall safety on the internet especially in DDoS attacks situations.
This type of cybercrime is quickly evolving relying on botnets, open-source network stress testing frameworks, scams, and other means. Therefore, organizations should have effective defenses in place to emerge unscathed if the disaster strikes.
What’s Next?
Preventing DDoS requires a multilayer strategy – auditing networks and apps, leveraging provider capabilities, and implementing intelligent prevention.
As attacks rapidly evolve, expert guidance is vital.
SpdLoad provides end-to-end security services to assess risks, architect robust defenses, and respond to incidents. Our certified team can audit your infrastructure, recommend proven solutions, and deliver ongoing management.
Contact us today for a free consultation on shoring up your DDoS defence.
Before making a hiring decision, explore the cost of hiring a software developer and what factors to consider.
Don’t let DDoS disrupt your business.
Planning your own business? Here are essential business startup tips to guide you.